emnify and AWS IoT - how to use them together
Sometimes the best connectivity solution is realized by bringing two systems together. In light of this - and with the recent launch of AWS IoT out of beta - we have put together an overview of the AWS offering as well as our own emnify Enterprise Connect (EEC) offer, showing you how they can be used together.
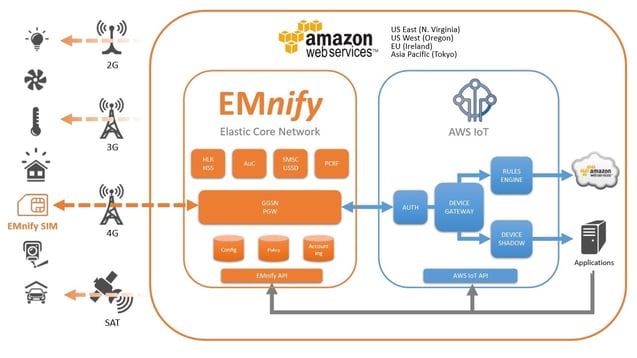
For the purposes of this document, we will refer to own enterprise connectivity solution as emnify Enterprise Connect (EEC). EEC is a fully scalable, pay-as-you-grow system that connects Machine to Machine devices globally using provider-agnostic M2M SIM cards in combination with a custom built mobile core network. It is a next-generation SaaS and IaaS platform that enables businesses to monitor, control and monetize their IoT ventures.
AWS IoT
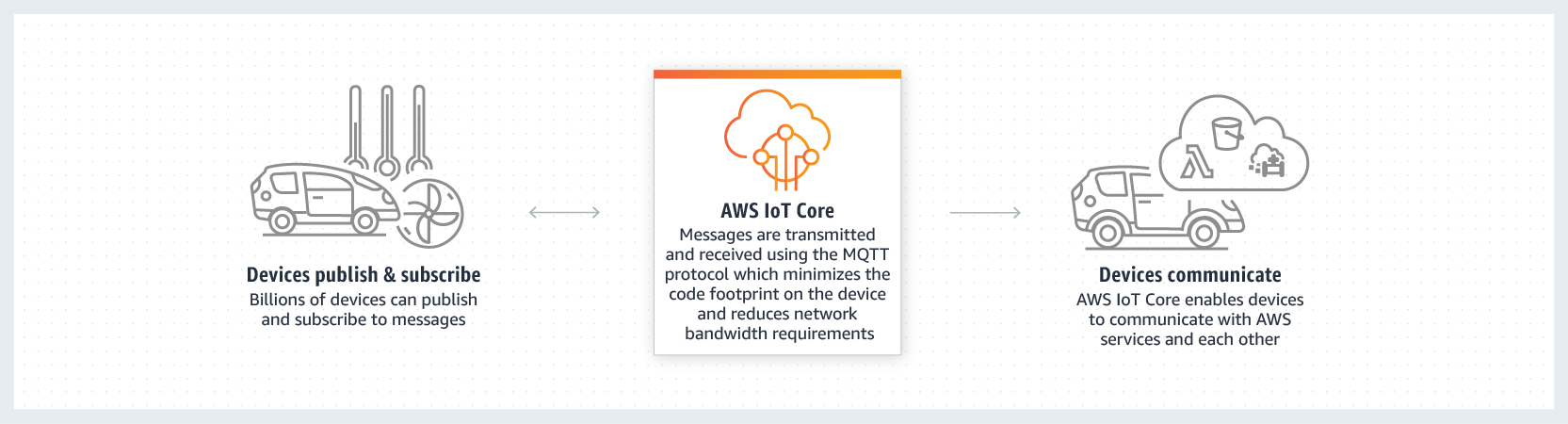
AWS IoT enables your IoT and M2M devices to communicate between themselves as well as with AWS Services and other cloud services. Amazon launched the service earlier in 2015 and as of December 2015 it is now out of beta and generally available.
Amazon provides you with with the following components:
IoT Device SDK
The AWS IoT SDK is currently available for C, JavaScript and the Arduino platform and it supports the MQTT or HTTP protocols. Certainly, you can also write your own implementation or use some open source alternative.
Device Gateway
The Device Gateway Service provides you with a messaging bus, operating similar to a messaging queue. It follows a publish and subscribe model, so your devices can publish messages on a specific topic and multiple subscribers can work with these messages.
Authentication and Authorization
AWS IoT also gives you an authentication and authorization service that can prove the identity of your IoT devices in a mutual way; this is used to encrypt data while being transmitted. For now, only the AWS method of authentication (named ‘SigV4’) and X.509 certificate based authentication is supported.
Registry
As many other IoT platforms, AWS also gives you the option to create some identity registry for your devices, it allows freely to add attributes to each device and to define its capabilities.
Device Shadows
A very useful feature of AWS IoT are Device Shadows. These represent a virtual version of a device, including its latest stage. This means that if the device is offline, applications or other devices can still interact with it and determine its past and future state.
Rules Engine
Once you connect your devices and they are exchanging data, you also need to store that data, process and analyze it further - and possibly even initiate some action based on it. This is where the Rules Engine comes into play; here you can define rules that look at incoming data and then apply modification and finally forward to them to other devices or cloud services.
emnify Enterprise Connect (EEC)
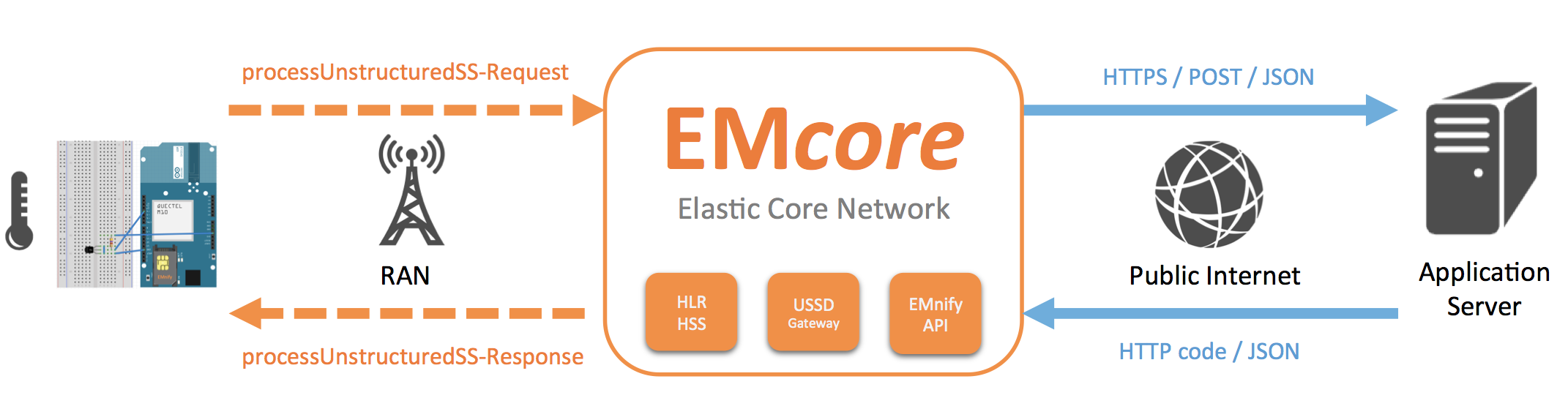
While AWS IoT provides excellent facilities to collect and process data from your IoT devices, emnify Enterprise Connect (EEC) provides your devices with the complementary network connectivity. This includes the data backhaul into AWS, managing and control functions and the global network access.
SIM Technology
emnify M2M SIMs fit into the GSM modules of your IoT devices and come with network agnostic and operator independent mobile connectivity into 2/3/4G and satellite networks. Available in all form-factors, including the latest embedded SIM options - and industrial grade versions made for harsh environments - they are perfect for large-scale and high quality IoT projects.
Global Data Transport
emnify SIMs connect your devices to an underlying network infrastructure that is purpose built for global distributed communication and provides you with regional and domestic data transport for your devices on global scale, in a secure way.
Global Network Access
With emnify, you gain unified and seamless cellular network access on a global scale - spanning more than 160 countries with multiple radio networks per country
Easy and secure integration
The integration between AWS IoT and EEC is easy and straight-forward as EEC is pre-integrated into the AWS infrastructure.
Also, with the tight network integration your devices can enjoy highest quality of service and low latency data transport, wherever they are deployed. Data streams stay inside the AWS environment and are not transferred over the public internet.
Global Availability
emnify Enterprise Connect and AWS IoT is available in the following AWS regions.
- US East (N. Virginia)
- US West (Oregon)
- EU (Ireland)
- Asia Pacific (Tokyo)
Connecting a device
The easiest way to connect your devices is to use one of the SDKs provided by Amazon, they are currently available for the following platforms:
- Embedded C
- NodeJS
- Arduino Yún
Creating a thing
To get started, you need to log into your AWS console, go to “Services” and then “AWS IoT”.
From here you can instantly select “Create a resource” and then “Create a thing”, just give it a name as you like and you can add the attributes later on.
Once created, the system will offer you to connect your devices first so choose “Connect a device”, and then the SDK you want to use.
In the following paragraphs we will use the NodeJS SDK to run some sample code, this would be suitable for a setup on a Raspberry Pi for example.
The system will offer you three download links
- Download public key
- Download private key
- Download certificate
Please download all of these and store the files in a secure place, you will need them further down the track to get your device connected and authenticated.
After you click on “Confirm & start using” the system will offer you some JSON content you can use as a default configuration. Simply Copy and Paste this content into a new file on your machine. For example, you can name the file with the identifier of your devices as ad3XXXXXXX.json, the content will look like this:
{
"host": "A38PYDNFBGK08J.iot.eu-west-1.amazonaws.com",
"port": 8883,
"clientId": "bulb",
"thingName": "bulb",
"caCert": "root-CA.crt",
"clientCert": "ad3XXXXXXX-certificate.pem.crt",
"privateKey": "ad3XXXXXXX-private.pem.key"
}
Configuring Mobile Connectivity
The NodeJS SDK works smoothly when your device is attached to a mobile network and connecting through emnify’s Elastic Core Network. In order to fit your device with mobile connectivity, you will need to have an emnify M2M SIM at hand and a GSM module connected.
You can find detailed information on how to set this up in our separate blog post “How to fit a Raspberry Pi with mobile M2M connectivity”.
Using the NodeJS SDK
Installing the NodeJS SDK
via npm
npm install aws-iot-device-sdk
or from GitHub
git clone https://github.com/aws/aws-iot-device-sdk-js.git
cd aws-iot-device-sdk-js
npm install
Adding a sample device configuration
{
"host": "A38PYDNFBGK08J.iot.eu-west-1.amazonaws.com",
"port": 8883,
"clientId": "bulb",
"thingName": "bulb",
"caCert": "root-CA.crt",
"clientCert": "ad3XXXXXXX-certificate.pem.crt",
"privateKey": "ad3XXXXXXX-private.pem.key"
}
The “root-CA.cert” you will need to download from Symantec, you can find it at the following URL https://www.symantec.com/content/en/us/enterprise/verisign/roots/VeriSign-Class%203-Public-Primary-Certification-Authority-G5.pem, just download it and store it as “root-CA.crt".
Running the code examples
The SDK includes ready-to-run code examples that let you quickly test your device’s ability to connect.
You can make use of the auto-generated configuration file but it is important to specify on the command-line the region where you have created your device, otherwise the SSL handshaking will fail due to an invalid client certificate (the default region is “us-east-1”).
Actually, we will start two instances of the device-example.js script, one in with test-mode=1 and one with test-mode=2:
First Instance
node examples/device-example.js -F ad3XXXXXXX.json -g eu-west-1 --test-mode=1
connect
message topic_1 {"mode2Process":1}
message topic_1 {"mode2Process":2}
message topic_1 {"mode2Process":3}
Second Instance
node examples/device-example.js -F ad3XXXXXXX.json -g eu-west-1 --test-mode=2
connect
message topic_2 {"mode1Process":7}
message topic_2 {"mode1Process":8}
message topic_2 {"mode1Process":9}
message topic_2 {"mode1Process":10}
This sample code demonstrates a simple publish and subscribe scenario, after the connect message you will see a continuous stream of messages being exchanged.
Tracking connectivity state, geo-location and data usage
When using AWS IoT in combination with emnify you have deep insight the into the connectivity state, geo-location info and usage data statistics through the emnify API.
Retrieving usage data
By making use of the NodeJS “request” module to connect to the emnify RestAPI your scripts will gain access to all network and connectivity related data, in the following you see the code to retrieve the latest usage statistics in real-time:
var request = require("request");
var options = {
method: 'GET',
url: 'https://cdn.emnify.net/api/v1/endpoint/73889922/stats',
headers: {
'cache-control': 'no-cache',
authorization: 'Bearer YOUREMNIFYAPITOKEN'
}
};
request(options, function(error, response, body) {
if (error) throw new Error(error);
console.log(body);
});
JSON Object
{
"current_month": {
"data": {
"endpoint": {
"id": 3992
},
"month": "2015-12-01",
"volume": "1.992463",
"volume_tx": "0.531732",
"volume_rx": "1.460731",
"last_updated": "2015-12-28 09:18:28",
"cost": "0.0988694500",
"id": 505,
"traffic_type": {
"description": "Data",
"unit": "MB",
"id": 5
},
"currency": {
"code": "EUR",
"symbol": "€",
"id": 1
}
}
}
}
Geo-Location
Also the geo-location is available in real-time and the resulting JavaScript object can be published on AWS IoT:
var request = require("request");
var options = {
method: 'GET',
url: 'https://cdn.emnify.net/api/v1/endpoint/73889922/location',
headers: {
'cache-control': 'no-cache',
authorization: 'Bearer YOUREMNIFYAPITOKEN'
}
};
request(options, function(error, response, body) {
if (error) throw new Error(error);
console.log(body);
});
JSON Output
{
"gcid": "262-01-34822-43418",
"lat": 49.80419710,
"lng": 10.00566730
}
Working with rules
Rules on AWS IoT allow you to route data from your connected devices to some other services. A rule consists of a name, an optional description, a SQL statement and one or more actions.
The SQL statement actually uses a simplified SQL syntax to filter messages, plus you can add a filter to look for specific MQTT topics and a condition when the rule should trigger.
Finally you can add more actions, currently you have the following options
- AWS Lambda
- Amazon Kinesis
- Amazon S3
- Amazon Machine Learning
- Amazon DynamoDB
- Amazon Simple Notification Service (SNS)
For example, if you want to store the location data as retrieved on the previous sample from the emnify API persistently then you could choose the DynamoDB as the action.
This can also be done via the AWS CLI by uploading content from an JSON file
aws iot create-topic-rule --rule-name my-rule --topic-rule-payload file://my-rule.json
{
"sql": "SELECT * FROM 'iot/test'",
"ruleDisabled": false,
"actions": [{
"dynamoDB": {
"tableName": "my-dynamodb-table",
"roleArn": "arn:aws:iam::123456789012:role/my-iot-role",
"hashKeyField": "topic",
"hashKeyValue": "${topic(2)}",
"rangeKeyField": "timestamp",
"rangeKeyValue": "${timestamp()}"
}
}]
}
Other interesting use cases are:
- trigger some action based on the location of a device using AWS Lambda
- send alerts based on connectivity state and data usage
- send and receive SMS to/from the device
Conclusion
With AWS IoT, Amazon has added another important building block to their portfolio cloud services. The functionality you needed in the past to use multiple service providers can now be created on single platform.
There’s great potential for Amazon to attract a large developer community in the future, particularly if it continues to add support for more platforms and SDKs. As AWS IoT comes with an open architecture and can be easily combined with other cloud services, such as emnify, it gives developers access to a very powerful and secure infrastructure that will scale to billions of devices.
For more information about the AWS IoT please see the Amazon website. You can also sign up to our newsletter to keep up with the latest news and insights
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

Joe is an experienced engineer in the field of telecommunication systems, applications and IoT. He is currently supporting the sales team for all things technical and is a valued member of the emnify family.