
The Raspberry Pi is a great platform to prototype and realize projects for IoT. Network connectivity can easily be established via its build-in Ethernet interface or an optional Wifi dongle.
Although, when it comes to projects that need mobile connectivity, things can get a little bit more complicated in terms of device configuration, remotely controlling the network access and choosing the right mobile provider to ensure a reliable, secure and cost-efficient setup.
In our blog post we will guide you through the steps to set up, monitor and control mobile M2M connectivity on the Raspberry Pi using a Huawei USB Modem E398 fitted with the emnify M2M SIM.
Hardware Requirements
- Raspberry Pi installed with Raspbian OS
- Huawei LTE USB Modem E173
- EMnify M2M SIM
Required Debian Packages
- ppp - Point-to-Point Protocol (PPP) – daemon
- usb-modeswitch – mode switching tool for controlling “flip flop” USB devices
- usb-modeswitch-data – mode switching data for USB-modeswitch
You can install these packages via apt-get. To do so, log in as ‘root’ to the Raspberry Pi and run the following command:apt-get install ppp usb-modeswitch usb-modeswitch-data
Configure Huawei USB Stick
The Huawei stick can work in two different modes: storage and modem. To work together with the PPP Daemon we need to ensure it is switched to modem mode on startup, the usb-modeswitch tool will do this for you, but first you need to find the vendor and product ID, so that you can add the correct usb-modeswitch configuration.
Plug in the USB and then run lsusb, you should see the following output
root@sn-box:~# lsusb
Bus 003 Device 003: ID 12d1:1436 Huawei Technologies Co., Ltd. Broadband stick
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 002 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Bus 003 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 004 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
Now we need to add the required configuration to /etc/usb_modeswitch.conf
DefaultVendor=0x12d1DefaultProduct=0x1436
MessageEndpoint="0x01"
MessageContent="55534243123456780000000000000011062000000101000100000000000000"
To check if it is working you need to reboot the Raspberry Pi and - if it has worked correctly - you will find the log messages about the switching in /var/log/syslog
May 11 21:56:36 sn-box usb_modeswitch: switching device 12d1:1446 on 001/007
May 11 21:56:36 sn-box kernel: [ 533.141948] ehci_irq: port change detect
May 11 21:56:36 sn-box kernel: [ 533.145965] usb 1-1: USB disconnect, device number 7
May 11 21:56:39 sn-box kernel: [ 536.982223] ehci_irq: port change detect
May 11 21:56:40 sn-box kernel: [ 537.261862] usb 1-1: new high-speed USB device number 8 using sw-ehci
May 11 21:56:40 sn-box kernel: [ 537.424772] usb 1-1: New USB device found, idVendor=12d1, idProduct=1436
May 11 21:56:40 sn-box kernel: [ 537.444195] usb 1-1: New USB device strings: Mfr=4, Product=3, SerialNumber=0
May 11 21:56:40 sn-box kernel: [ 537.461071] usb 1-1: Product: HUAWEI Mobile
May 11 21:56:40 sn-box kernel: [ 537.475642] usb 1-1: Manufacturer: HUAWEI Technology
May 11 21:56:40 sn-box kernel: [ 537.496180] option 1-1:1.0: GSM modem (1-port) converter detected
May 11 21:56:40 sn-box kernel: [ 537.515557] usb 1-1: GSM modem (1-port) converter now attached to ttyUSB0
May 11 21:56:40 sn-box kernel: [ 537.542851] cdc_ether 1-1:1.1: wwan0: register 'cdc_ether' at usb-sw-ehci-1, Mobile Broadband Network Device, 02:50:f3:00:00:00
May 11 21:56:41 sn-box logger: usb_modeswitch: switched to 12d1:1436 on 001/008
Add ppp interface configuration
In the next step we add a new interface configuration to enable the ppp interface in /etc/network/interfaces
auto gprs
iface gprs inet ppp
provider gprs
and we add a corresponding peer configuration file ‘gprs’ in /etc/ppp/peers
user "emnify"
connect "/usr/sbin/chat -v -f /etc/chatscripts/gprs -T em"
/dev/ttyUSB0
noipdefault
defaultroute
replacedefaultroute
hide-password
noauth
persist
usepeerdns
Start the ppp interface
ifup gprs
Now the pppd will initialize the modem and start the ppp connection, if everything went fine you will see a ppp0 interface with IP address assigned and corresponding entries in the routing table:
root@sn-box:~# ifconfig ppp0
ppp0 Link encap:Point-to-Point Protocol
inet addr:10.199.1.38 P-t-P:10.64.64.64 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:499 errors:0 dropped:0 overruns:0 frame:0
TX packets:591 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:3
RX bytes:66122 (64.5 KiB) TX bytes:99537 (97.2 KiB)
root@sn-box:~# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 0.0.0.0 0.0.0.0 U 0 0 0 ppp0
10.64.64.64 0.0.0.0 255.255.255.255 UH 0 0 0 ppp0
… let’s check if you’re connected to the internet:
>root@sn-box:~# ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_req=1 ttl=55 time=101 ms
64 bytes from 8.8.8.8: icmp_req=2 ttl=55 time=99.5 ms
64 bytes from 8.8.8.8: icmp_req=3 ttl=55 time=98.2 ms
From now on the Raspberry Pi will automatically connect on startup and also retry to connect in case the connection is lost or interrupted.
Monitor M2M connectivity in the emnify Portal
Through fitting our Raspberry Pi with an emnify M2M SIM we can control and monitor its network connectivity in real-time using the emnify Portal. It allows us to check the current connectivity status, location and on-going data usage:
[gallery columns="2" size="medium" link="file" ids="24270,24271"]
Control network access remotely
Imagine you have deployed your Raspberry Pi on a remote location and you want to temporary disable network access due to security or cost reasons.
Doing this on application level requires remote access and reactivation at a later stage can be tricky. The emnify IoT Portal allows you to perform this task with a single mouse click. Use the “Disable” button and your Raspberry Pi will be instantly and securely disconnected from the network.

The PPP Daemon on the Raspberry Pi will recognise this nicely and shutdown the connection.
Jun 18 12:17:05 sn-box pppd[14614]: Modem hangup
Jun 18 12:17:05 sn-box pppd[14614]: Connection terminated.
Jun 18 12:17:06 sn-box pppd[14614]: Script /etc/ppp/ip-down finished (pid 15807), status = 0x0
This will also be reflected in real-time on the emnify IoT Portal
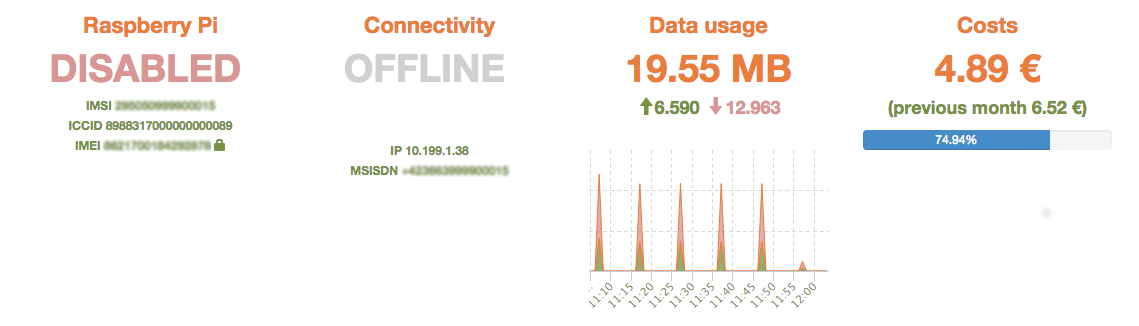
Also if you want to enable network access again at a later stage you can use the “Enable” button in the emnify IoT Portal and your Raspberry Pi will turn back online.
In our blog post you have seen how easy it is to connect and control the M2M network connectivity of a Raspberry Pi when managed through the emnify IoT Platform.
In our next posts we will elaborate on how to use the advanced features of the emnify Platform to provision endpoints and SIM cards, to set up usage policies and manage these functions in an automated way through our API.
In the meantime, if you have questions about our services or are looking for reliable and secure mobile connectivity for your M2M/IoT devices, please send us an email via our contact page.

The content team of emnify is specialized in all things IoT. Feel free to reach out to us if you have any question.

.png)