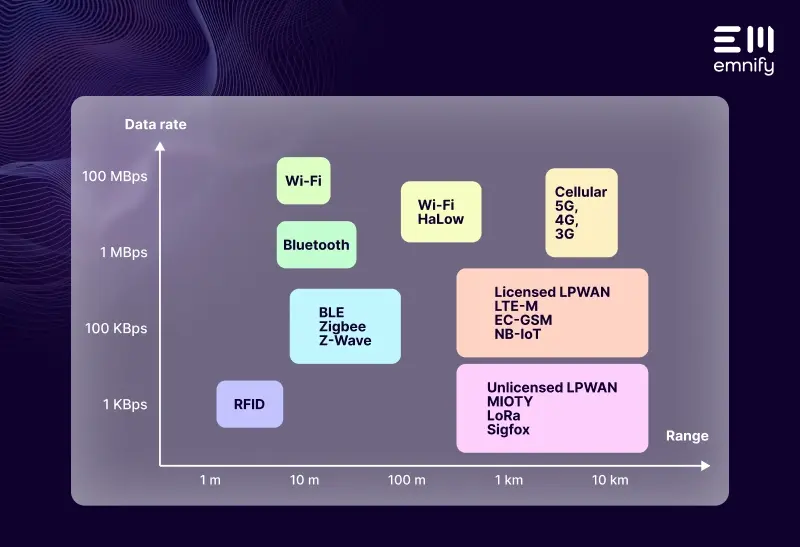
Quick definition: Internet Protocol Security (IPsec) is a protocol suite that secures network communications at the IP layer. It facilitates two-way authentication between network entities exchanging data, then uses keys to authorize data packets.
Internet Protocol Security (IPsec) is one of the key layers of protocols developers use to secure the exchange of data through a network. (If you wish to know more about protocols and IoT check out our Comprehensive Guide to IoT Protocols.)
In cellular IoT, IPsec closes the public Internet gap between the mobile network and the application infrastructure. With IPsec, the device itself doesn’t need to handle encryption, so data exchanges use less processing power and consume less data. This is especially valuable for devices that don’t have the resources to encrypt transmissions with Transport Layer Security and Secure Sockets Layer (TLS/SSL).
Even for devices with end-2-end encryption, IPsec can provide an additional layer of security by making sure the device and application are not exposed to the public internet.
The scope of IP security depends on whether you use the protocol suite in “transport mode” or “tunnel mode.” Transport mode merely secures the information being transported, while tunnel mode completely secures the traffic sent between network entities. (Tunnel mode is a method of creating Virtual Private Networks.)
Here’s how IPsec secures your network communications.
The three IPsec protocols
IPsec includes three distinct protocols that secure different aspects of network communications:
- Authentication Headers (AH)
- Encapsulating Security Payloads (ESP)
- Internet Security Association and Key Management Protocol (ISAKMP)
Authentication Headers and Encapsulating Security Payloads can be used together or separately, and ISAKMP reacts to which of these protocols are used for the transmission.
Authentication Headers
When devices, applications, and network entities exchange data packets, there are opportunities for bad actors to intercept or alter them before they reach their destination. Hackers can also create fraudulent data packets to pass malware to your devices.
An Authentication Header helps the network verify where a packet came from and whether the transmission has been modified. Authentication Headers use a shared key to verify the sender’s identity and a checksum to confirm the data’s integrity.
In a “replay attack,” a hacker sends copies of packets as part of a Denial of Service attack. Optionally, Authentication Headers can include a sequence number to ensure that the specific packet hasn’t already been received, which can help prevent this kind of attack.
Encapsulating Security Payloads
While Authentication Headers verify the identity of the sender and receiver and detect altered packets, Encapsulating Security Payloads adds encryption and another layer of authentication. It’s like putting privacy glass over the data transmission to prevent anyone from seeing what’s inside.
When IPsec is used in transport mode, ESP only “encapsulates” the data payload—the header is still readable. In tunnel mode, however, ESP encapsulates the entire data packet and attaches a new header on the outside. This outer header is all that’s visible without authentication and the encryption key.
Internet Security Association and Key Management Protocol
IPsec uses ISAKMP to define the security attributes two network entities will use to exchange data. Before the transmission is sent, the two parties establish the duration of the session, the algorithms they’ll use to encrypt the data packet, and the keys they’ll use to authenticate it.
Tunnel mode vs. transport mode
While transport mode only secures the data being transmitted, tunnel mode creates an encrypted connection between two network entities. Tunnel mode is the most common usage of IPsec and works well for connecting two different networks together—such as a customer’s network and your own—to create a VPN.
IPsec vs. TLS/SSL
Transport Layer Security and Secure Sockets Layer (TLS/SSL) protocols secure communications at the application layer, while IPsec secures communication at the IP layer.
This means that TLS/SSL only secures communications to and from the protected application. Other devices on the network remain insecure, as do other applications. IPsec secures all data from all devices in a network and enables them to communicate securely with devices and applications on another network.
Secure your IoT connectivity with emnify
emnify is a world-class IoT communication platform. We use cellular connectivity with network-level security to protect your connections and keep your communications secure. We bolster your IoT security with network firewalls, IMEI locks, limited connectivity profiles, abnormality detection, and more.
When you use emnify, all your devices are in a private network behind a carrier grade NAT, and they can only be reached through a VPN. With IPsec, there’s just one connection between the mobile network and the application infrastructure. So your devices can securely communicate with the MQTT broker, DNS server, or the server with firmware updates from the same connection, and there’s no need to manage multiple certificates.
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

If you want to understand how emnify customers are using the platform Christian has the insights. With a clear vision to build the most reliable and secure cellular network that can be controlled by IoT businesses Christian is leading the emnify product network team.