Coined by Gartner in the 2019 Networking Hype Cycle and Market Trends report, Secure Access Service Edge (SASE) introduces a new architecture where networking and security functions are bundled in a cloud-delivered service. As IoT and internet-based traffic continues to soar, SASE allows enterprises to streamline network integration, security, and policy management of distributed devices with a centrally managed platform.
Security Headaches in IoT Communication
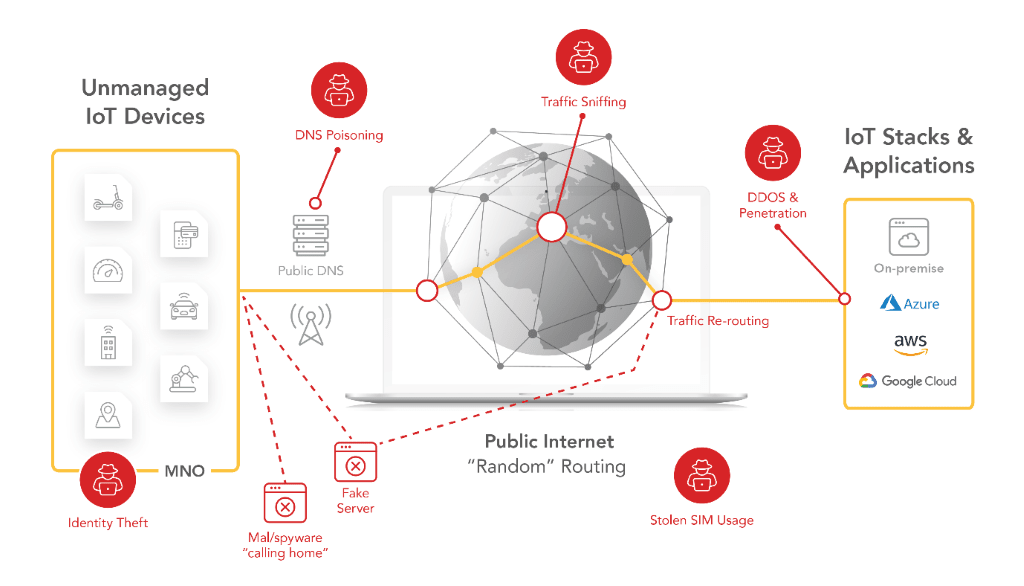
The number of IoT devices is growing exponentially, but security has failed to keep pace. Among the 1.2 billion devices communicating through cellular networks in 2020 (Gartner), most of them are exposed to the risk of unmanaged and poorly secured connectivity. Indeed, a recent report by Palo Alto Networks stated that 98% of all IoT traffic is unencrypted, and 57% of IoT devices are subject to medium- or high-severity breaches. Before we know it, connected devices have become the low-hanging fruit for attackers to exploit.
Devices using the public Internet are vulnerable to wide-ranging potential attacks that threaten the integrity and security of highly sensitive IoT data.
- Eavesdropping and traffic sniffing: Unencrypted transmissions allow attackers to read, steal and alter messages.
- DNS poisoning: Compromised public Domain Name Systems divert device communication to false application servers instead of legitimate ones.
- Calling home: Malware or third-party firmware on the device intentionally or unintentionally calls home and sends data to third parties without the user’s knowledge.
- Distributed Denial of Service: A server is congested and becomes unavailable for the intended traffic, as the attacker overloads it with influxes of redundant requests. The use of dynamic public IP addresses for devices impedes the application firewall from properly filtering unwanted traffic.
- Unprotected SIM: Devices deployed in public areas are prone to SIM theft for free data usage on another device, or worse, unauthorized access to a platform if SIM is used as the device identity.
Why IoT Needs a New Security Approach
In traditional IoT connectivity models, communication access and authentication are driven by a service provider's home network – forcing the traffic to first route through the central home network to break out through the public internet to the application location. Complex setup of dedicated endpoint clients is often required to establish a VPN connection or SSL/TLS encryption between the endpoint and the central IoT application. What’s more, standalone devices mostly rely on local configuration settings to control network activities.
Nevertheless, in the IoT age where vast devices are geographically distributed and data is dispersed across multi-region cloud and SaaS applications, such an architecture quickly reaches its limitation. Complexity and latency challenges become evident as the need for local data processing regulations continues to rise. In this context, SASE presents a cloud-native framework that matches emerging IoT requirements to streamline edge security, networking, and operations of connected devices.
SASE – Localized, identity-driven security services with a global cloud-native platform
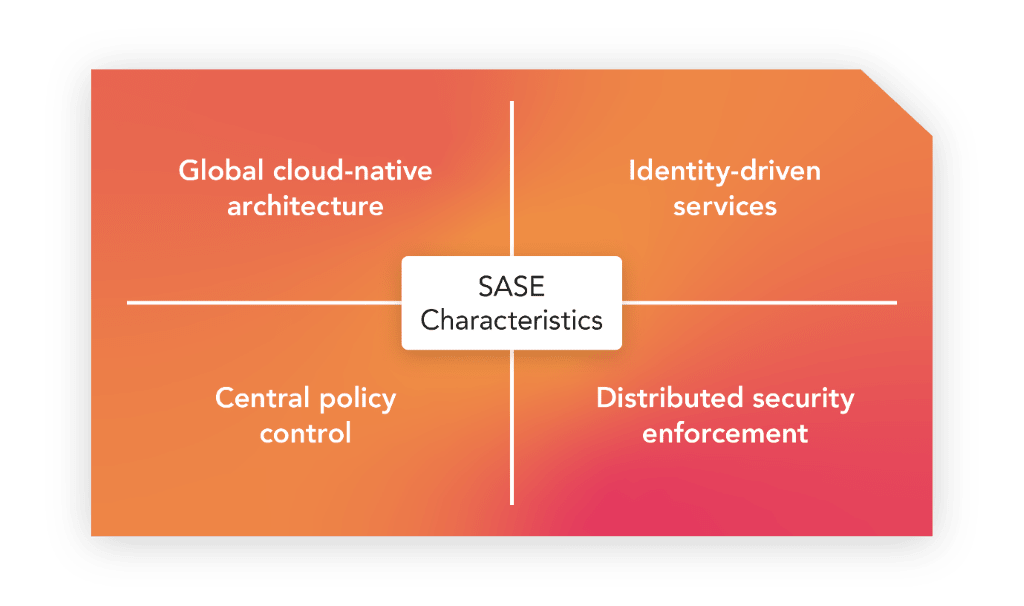
Simply speaking, SASE converges multiple virtualized networking and security capabilities into one unified, easy-to-consume cloud service. Secure access is delivered through centralized policy control that enables optimized, shortest-path data routing and protected traffic to the application - regardless of where devices, service provider network, and IoT applications are located.
In the SASE model, security checkpoints are shifted closer to the data source. Policies are enforced at distributed points of presence (PoP), where access is granted based on the identity of connected entities (IoT devices) such as a specific device attribute or its location. The edge or PoPs can be the SASE vendor’s data centers/ cloud regions close to devices and the application server. With policies easily programmable to tailor to each unique application, a high level of automation can be achieved.
The combination of cloud-based, centralized policy management and local enforcement of identity-driven SASE services brings great benefits to IoT users. The former streamlines cost and complexity as network security services can be consolidated with a single vendor, and businesses can have a single view of all device communication. The latter helps to minimize network latency while allowing IoT enterprises to comply with customers‘ local data processing requirements and benefit from high-performance security at the edge. As legacy VPN is replaced with automated, cloud-native security features, there are fewer clients required on a device.
 SASE Services for IoT
SASE Services for IoT
The breadth of network and security features in a SASE architecture is far-reaching and vastly varies across vendors. Below are several pillars you should look for in a SASE solution for IoT.
- Dynamic Data Routing with Software-Defined Wide Area Network (SD-WAN)
A SASE service integrates network access and traffic optimization in a globally distributed infrastructure comprised of multi-regional PoPs. With access control and security policy enforcement delivered as a cloud service, there is no need to divert traffic through a service provider’s home network. Instead, device data is routed to the local SASE PoP and user application infrastructure to improve the performance and latency of the IoT application. - Firewall as a Service (FaaS)
Amid increasingly distributed IoT resources, a cloud-based network firewall can act as a distributed line of defense to filter out unwanted Internet traffic and protect edge devices and IoT applications. Instead of leaving the configuration to the edge device or the central IoT application – a network firewall eliminates on the connectivity layer illegitimate traffic over the public internet, while legitimate targets can be whitelisted. This prevents devices from communicating with malicious servers and domains used in security breaches like home calling and traffic rerouting with DNS spoofing. - Cloud Access Security Broker (CASB)
A CASB ensures secure data transport into multiple cloud environments through encryption to avoid eavesdropping and data thefts. In IoT, advanced solutions can establish automatic, private connections between devices, the SASE platform, and user’s VPC using private static IPs and cloud-native services like AWS Transit Gateway. That way, data is securely brought into the cloud infrastructure without using the public Internet and remains invisible from the outside world. - DNS Security
A SASE solution can help to protect DNS integrity and availability by allowing users to configure and utilize their trusted DNS service. For example, IoT enterprises with applications deployed in the cloud can use the private DNS server of their cloud infrastructure that is inaccessible from the public Internet. - Threat Detection
With so many components intertwined in an IoT solution, threat monitoring is central to security design. Yet, malware detection software is often a burden for IoT devices with limited processing capability. SASE services provide complete network visibility and fine-grained event metrics to help enterprises detect and trace the root cause of abnormalities and vulnerabilities in their IoT solution.
Summing Up
Originally developed to address changing enterprise security requirements for an increasingly remote workforce, the implication of a SASE architecture goes double for IoT. With more and more IoT applications shifting to the cloud and devices vastly dispersed, the combination of cloud-native security tools, local policy enforcement, and enhanced visibility makes SASE a winning use case. The marriage of network and security functions in a single management console allows enterprises to better protect their devices at reduced cost and complexity.
At emnify, we deliver a SASE-driven architecture using SIM as device identity to offer network and security-as-a-service for globally distributed resources. Contact us if you are interested in learning more about our solution.
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

Nhu has over six years of experience working with networking technologies and IoT connectivity solutions. She’s an avid tech learner with a customer-focused mindset.