Quick definition: Transport Layer Security (TLS) is the most widely used security protocol for communications over the Internet. TLS provides three main functions: authentication, encryption, and verification. It encrypts transmissions using a system of certificates and keys, verifies both network entities are authorized to transmit/receive data, and ensures the data hasn’t been corrupted.
As the name implies, Transport Layer Security is a protocol that gets implemented on the transport layer of a network to encrypt data transmitted via HTTP, FTP, XMPP, etc. TLS is typically implemented in conjunction with protocols like Transmission Control Protocol (TCP), which prioritizes accuracy over speed. However, in some cases it can be used with connection less protocols like User Datagram Protocol (UDP) - then using a slight variant called DTLS.
Any time you see HTTPS, your connection is being secured via TLS—but it has many other use cases, too. While TLS is best known for providing secure exchanges between computers and web browsers, billions of Internet of Things devices rely on this security protocol as well. Here’s what you should know about this important protocol.TLS evolved from SSL
First proposed by the Internet Engineering Task Force (IETF) in 1999, TLS has undergone several iterations, the latest of which is TLS 1.3, published in 2018. TLS is the direct descendant of another well-known security protocol: Secure Sockets Layer (SSL). The first release of TLS was originally called SSL 3.1, but the IETF changed the name to disassociate it with Netscape, the developer of SSL.
The TLS specification notes that, “The differences between this protocol and SSL 3.0 are not dramatic, but they are significant enough that the various versions of TLS and SSL 3.0 do not interoperate”.
With security protocols, the newest versions typically address vulnerabilities in past releases. TLS 1.3 is the most secure, but older versions are still in use, and some technologies still rely on SSL—which is dangerously outdated.
How TLS works
TLS secures data transmissions by establishing a “handshake” between a client and a server. Through a series of back-and-forth communication, the client and server set up a TLS connection. During this process, the network entities confirm which version of TLS they’ll use to communicate, establish which suite of algorithms they’ll use to encrypt transmissions, and then exchange keys.
It’s sort of like when an account asks you a security question before you can log in—only the security question is actually a sequence of numbers, and the correct answer with a specific number based on an algorithm you can only know if you’re authorized to access the account.
This prevents unauthorized users from accessing your data packets. If they intercepted a transmission, they can’t see inside the packet without the key that decrypts your data.
Older versions of TLS use a more tedious (and time-consuming) process to authenticate the client and server, but TLS 1.3 has streamlined the handshake to reduce the amount of back-and-forth communication.
TLS and the Internet of Things
Cybersecurity is vital for IoT. Internet of Things devices often transmit highly sensitive data over the Internet, and unfortunately, this data is often unencrypted. TLS is an excellent solution for encryption, authentication, and ensuring data integrity, but the very process which makes it secure—the handshake—can make it difficult to implement on networks with low bandwidth, which IoT devices frequently rely on.
Since the handshake requires back-and-forth messaging in addition to the transmission itself, it can dramatically increase the power consumption of transmissions, reducing the battery life (and therefore overall life expectancy) of an IoT device.
It’s also common for IoT devices to communicate with a gateway, which serves as an intermediary between many devices and a server. The smart meter can privately communicate with the gateway, and then the gateway can use TLS or IPsec to encrypt and forward the transmission to the server. (This is one of the main approaches to smart meter communication.)
The difference between TLS and IPsec
The main difference between TLS and IPsec is that TLS works on the application level - and secures the communication between two services, whereas IPsec secures the connection between two networks or hosts.
If there are different services or applications in the same network or host - then the device would need to setup a TLS connection for every service with different keys. With IPsec the connection towards the network is secured and encrypted and only one is sufficient no matter how many applications are running over the IPsec.
Keep learning about IoT security
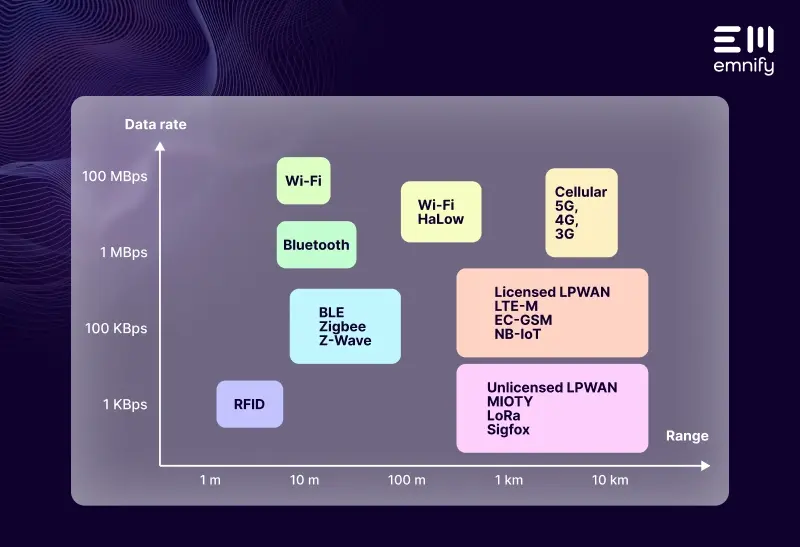
Transport Layer Security is one of many technologies for securing data transmissions sent over the public internet no matter if you use Wi-Fi, Lora, Ethernet or cellular. Many cloud IoT services from Amazon, Azure or Google do support certificate based TLS encryption.
Cellular IoT provides manufacturers with a range of additional security measures like SIMs, IMEI locks, network firewalls, connectivity profiles, and more.
To learn more about the risks associated with IoT security, examples of how hackers have taken advantage of these devices, and the solutions IoT manufactures are using, check out our introduction to IoT security.
And if you you wish to know more about protocols and IoT check out our Comprehensive Guide to IoT Protocols.
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

If you want to understand how emnify customers are using the platform Christian has the insights. With a clear vision to build the most reliable and secure cellular network that can be controlled by IoT businesses Christian is leading the emnify product network team.