
Quick definition: User Datagram Protocol (UDP) is a communications standard for exchanging data over the Internet. UDP prioritizes speed over reliability, using a connectionless process to send data packets to a destination. Due to its low latency, UDP is ideal for time-sensitive use cases like video streaming, Voice over Internet Protocol (VoIP), video gaming, and Domain Name System (DNS) lookups.
When higher-level protocols need to transmit data quickly, they rely on UDP to package and distribute that data over the Internet Protocol (IP). (If you wish to know more about protocols and IoT check out our Comprehensive Guide to IoT Protocols.)
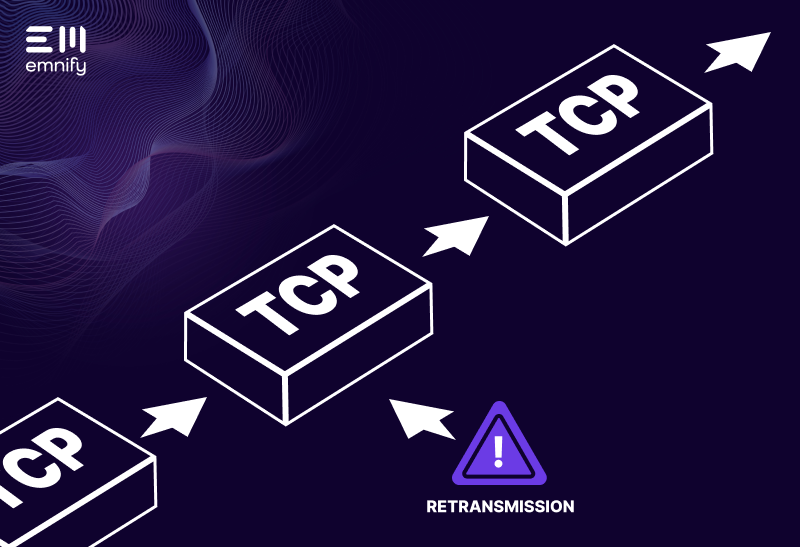
Unlike Transmission Control Protocol (TCP)—the most common protocol used for transmitting data over the Internet—UDP doesn’t order data packets or directly establish a connection between the endpoints, such as an IoT security camera and a smartphone. It also has no congestion control systems to optimize network resources. It simply gets data from Endpoint A to Endpoint B as quickly as possible.
When exchanging data over the Internet Protocol, data packets can often arrive out of order or get lost in transmission. TCP will request retransmissions of lost data packets and reorganize packets that arrive out of order. This increases accuracy, but it also increases latency, and if individual packets of an audio or video file get lost, humans often can’t even detect the errors. Retransmitting missing packets or reordering them when they arrive will only cause more interference in the real-time data stream.
UDP doesn’t correct errors, duplicates, or missing pieces. If a protocol uses UDP for transmitting data, data integrity is either unimportant, or the application itself has a process for checking against errors.
UDP headers
Like TCP, UDP labels data packets with a header. But UDP headers are much simpler. There are only four fields:
- Source port
- Destination port
- UDP length
- Checksum
The source port indicates where the transmission is coming from. The destination port indicates where it’s going. The UDP length specifies how many bytes the header and data represent. And the checksum is a field that can be used to check for errors in the header or data stream.
TCP has numerous additional fields in the header which help verify that the data packets arrive intact and can be rearranged as needed. These additional fields significantly increase the size of the header.
UDP in IoT
In IoT (and data transmission in general), User Datagram Protocol is less common than TCP. But UDP often appeals to IoT manufacturers because it uses fewer network resources to transmit and doesn’t have to maintain a constant connection between the two endpoints. In other words, it uses less data and consumes less power.
Resource constrained devices
IoT devices often operate within Low power, Lossy Networks (LLNs). LLNs are optimized for power efficiency, so they have very few resources. Constrained Application Protocol (CoAP) was specifically developed to help these devices communicate, and it runs on devices that use UDP.
Low downlink transmissions
UDP doesn’t send any acknowledgement that a transmission was received. The sender doesn’t know if the data packets arrived, but the exchange requires less downlink budget. For transmissions with low downlink allowances, UDP can be a valuable communication protocol.
Low power applications
In IoT, it’s often not a problem to lose a single datapoint because the device sends it periodically. Trying to resend the data drains more battery every time a datapoint gets lost or has an error. And since UDP doesn’t send an acknowledgement, the device can turn off faster after sending or receiving a transmission. This makes UDP appealing for developers who want to maximize power efficiency.
UDP security
While UDP is easy to implement and it has less overhead, it also leaves your devices more vulnerable to cyber attacks.
Since TCP establishes a direct connection and provides a sequence number, it’s more difficult for someone to send a packet to a specific application. With UDP, it’s easier to intercept, alter, and replicate data packets to attack a device, application, or network.
Additionally, botnets (massive networks of hacked computers, including IoT devices) can use UDP to send fraudulent packets to a computer. Bots will often spam transmissions to nonexistent ports, and the computer then has to send a response that the port is unavailable. This quickly takes network resources from legitimate data transmissions and can bring down the network.
With UDP, you need to be proactive about IoT security and be confident that your hardware and network-level security can protect your customers’ data and prevent your devices from becoming liabilities.
Get secure IoT connectivity with emnify
emnify is a communication platform dedicated to IoT. Not only can your devices connect through our global mobile network but the platform also ensures the security of your device. With advanced security features like private networks, network firewalls with IP whitelisting, and custom DNS we prevent common UDP attacks and make malicious communication with your device impossible.
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

If you want to understand how emnify customers are using the platform Christian has the insights. With a clear vision to build the most reliable and secure cellular network that can be controlled by IoT businesses Christian is leading the emnify product network team.