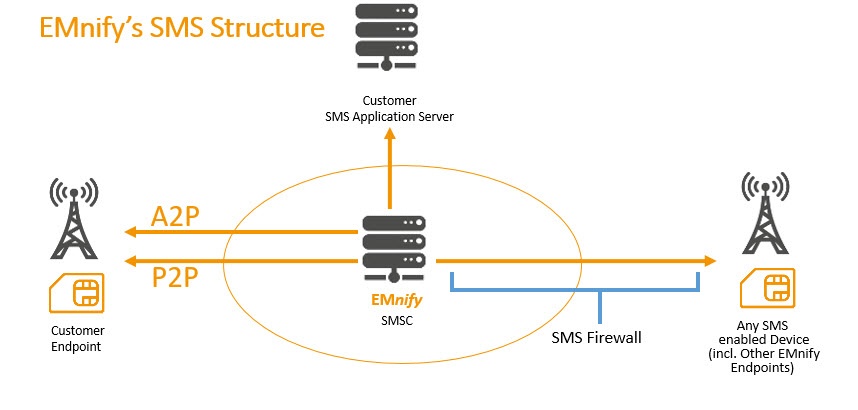
EMnify now offers enhanced SMS options for customers in the form of peer-to-peer (P2P) and application-to-peer (A2P) messaging. Combining these options increases flexibility and security for device configuration and communication.
SMS is an important feature for IoT and M2M developers and enterprises: is the only communication channel that works on every cellular-enabled device, on every network, and with full visibility of delivery status. SMS also works in areas of weak radio reception, and when a device is roaming. Although a single SMS is limited to 160 characters, multiple SMS can be logically grouped into one, making longer commands and message exchanges possible.
Both P2P and A2P messaging are necessary in IoT and M2M depending on the use case. P2P messaging could be required for an IoT device that sends alerts directly to the end user, such as a home smoke detector. A2P messaging would be more beneficial in use cases where data being sent to or from the device was controlled at the enterprise level, such as pipeline monitoring alerts.
In this blog post, we will explore both P2P and A2P messaging options, highlight security factors that should be taken into consideration, and share how customers can easily utilize one or both on the emnify platform.
Peer-to-Peer (P2P) Messaging
P2P is the exchange of SMS between devices. Devices address each other via telephone numbers (MSISDNs). P2P is the type of SMS that is sent between two mobile phones, and which consumers are most familiar with through basic text messages and group chats. P2P works through the default configuration in any cellular-enabled device, with no additional integration or setup required.
P2P messaging has limitations within an IoT and M2M context. First, automation is not possible. For example, if 10,000 devices need to be configured by SMS, manually keying in and sending a message to each of these devices would be incredibly difficult. Second, there is limited throughput of about 6 SMS per minute. If a number of messages needed to be sent, such as a series of alerts from a device, the messages could be delayed.
Most importantly, there are security issues surrounding P2P messaging, especially for IoT and M2M data of a sensitive nature. P2P messaging exposes devices to incoming messages from outside numbers - anyone in the world can access the device, sending commands and potentially changing the configuration settings. Building a secure SMS firewall is challenging without a robust service management platform like emnify.
Application-to-Peer Messaging
A2P is the exchange of SMS between a device and an application. Applications will connect to the device via an API, the emnify SMS console, or SMPP protocol (through the emnify SMS service center (SMSC)). Typically devices will address a Short Code to reach the application, which is a private number used to send SMS (3-6 digits) and is allocated by the customer. A2P works through the default configuration in any cellular-enabled device, although the application it communicates with must be set up separately.
A2P messaging is fully trackable, with oversight on the delivery status of a message. On the emnify platform, message status can be monitored through the emnify User Interface (EUI) SMS console and through the customer’s own application. Messages are instantly delivered through the emnify platform to a device that is attached to our network. A2P messages can be automated, which means customers with large numbers of deployments can easily configure their devices over-the-air.
Increasing Security through the emnify SMS Firewall
In general, A2P messaging is more secure than P2P, which has protection drawbacks. However, emnify is working to make both A2P and P2P messaging more secure by enabling our customers to control who their devices are allowed to communicate with.
As mentioned previously, P2P by default is an open messaging system and has no built-in verification of the authenticity of the sender, which means anyone with the MSISDN of the device can send messages to it and the originating address can easily be spoofed. Any system relying on the originating address for authentication are open to attacks by an SMS impersonating an authenticated phone number. However, emnify has enabled an SMS Firewall which means our customers have more control over device communication. Depending on the use case, customers can choose to:
- Enable open P2P communication
- Send P2P messages only to other customer devices (with emnify MSISDNs)
- Send P2P messages only to non-customer devices (non-emnify MSISDNs)
- Block any incoming P2P SMS to the device (i.e., mobile terminated/MT)
- Block any P2P SMS being sent from the device (i.e., mobile originated/MO)
- Block all P2P SMS from device to avoid any SMS-related charges
A2P messaging on the emnify platform is a closed communication system between a customer’s device and a customer’s application. Messages are directly routed (not through a 3rd party) and there is no access permitted outside of the customer device, customer application, and the emnify platform. A2P messages are sent and received via a RestAPI, emnify SMS console or SMPP protocol 3.4, both of which are set up and managed by the customer. Depending on the use case, customers can choose to:
- Send messages directly to customer devices (with emnify MSISDNs)
- Send messages directly to non-customer devices (non-emnify MSISDNs)
- Block all SMS from device to avoid any SMS-related charges
emnify customers can choose to have P2P enabled, A2P enabled, both P2P and A2P enabled, or SMS blocked account settings. If you would like to switch your current SMS account settings, please contact our support team at support.mnify.com.
Get in touch with our IoT experts
Discover how emnify can help you grow your business and talk to one of our IoT consultants today!

If you want to understand how emnify customers are using the platform Christian has the insights. With a clear vision to build the most reliable and secure cellular network that can be controlled by IoT businesses Christian is leading the emnify product network team.